#Day4 File Permissions and Access Control Lists:
Introduction:
In Linux, file permissions play a crucial role in maintaining the security of the system. File permissions determine who can access, modify, or execute a file or directory. In this blog, we will go through the different types of file permissions in Linux, how to change file permissions, and what are the best practices to follow.
File Permissions:
There are three types of file permissions in Linux:
Read (r): Allows a user to read the content of the file or directory. The read permission grants users and processes the ability to read the contents of a file or directory. For example, if a user has read permission on a file, they can view the contents of that file but cannot modify it.
Write (w): Allows a user to modify or delete the file or directory. Write permission (w): The write permission grants users and processes the ability to modify or delete a file or directory. For example, if a user has to write permission on a file, they can modify or delete the contents of that file.
Execute (x): Allows a user to execute the file or access the directory. The execute permission grants users and processes the ability to execute a file or access the contents of a directory. For example, if a user has executed permission on a file, they can run that file as a program. If a user has to execute permission on a directory, they can access the contents of that directory.

Regular file: A regular file contains data and is denoted by a hyphen (-) in the shell. For example, if you run the
ls -lcommand to list files and their permissions in a directory, a regular file will be displayed with a hyphen (-) in the first column.Directory: A directory is a container that can hold files and other directories, and is denoted by a letter d in the shell. For example, if you run the
ls -lcommand to list files and their permissions in a directory, a directory will be displayed with the letter d in the first column.Symbolic link: A symbolic link is a special type of file that points to another file or directory, and is denoted by an l in the shell. For example, if you run the
ls -lcommand to list files and their permissions in a directory, a symbolic link will be displayed with an l in the first column.
Symbolic Representation of Permission:
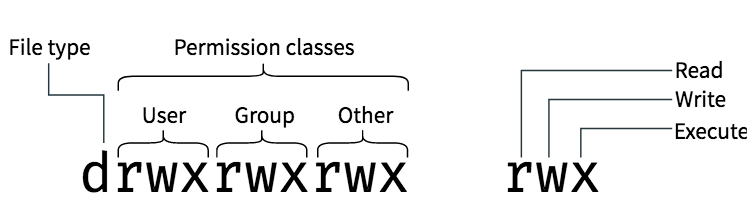
In Unix-like operating systems, file permissions can also be represented using a symbolic mode. The symbolic mode uses a combination of letters, operators, and permissions to represent the permissions for a file or directory.
The symbolic mode is represented by a combination of three different elements:
To who the permissions apply to:
"u" for the owner of the file
"g" for the group owner of the file
"o" for others (everyone else)
"a" for all (equivalent to "go")
The operation to be performed:
"+" to add a permission
"-" to remove a permission
"=" to set the permission to the exact value
The permission itself:
"r" for read permission
"w" for written permission
"x" for execute permission
Numeric Representation of Permissions:
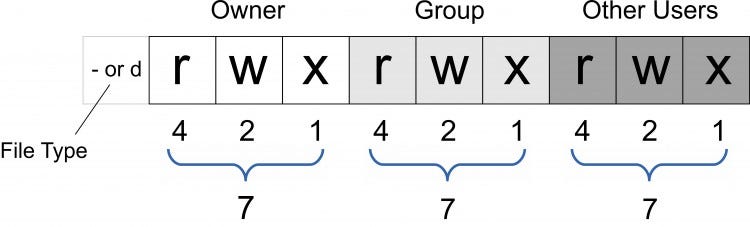
The numeric notation for permissions is calculated as follows:
Read permission is represented by the bit value 4 (100 binary)
Write permission is represented by the bit value 2 (010 binary)
Execute permission is represented by the bit value 1 (001 binary)
To calculate the numeric notation for a specific combination of permissions, you can add the values of the bits that represent each permission. For example:
To represent read and write permissions (but not execute permission), the numeric notation would be 6 (4+2).
To represent all permissions, the numeric notation would be 7 (4+2+1).
To represent read and execute permissions (but not write permission), the numeric notation would be 5 (4+1).
So, for example, if you see the permission set as rwxr-xr-- when listing a file or directory using the ls -l command, it means that the owner has read (r), write (w), and execute (x) permissions, the group has read (r) and execute (x) permissions, and others have only read (r) permission. In numeric notation, this would be represented as 750 (7 for the owner, 5 for the group, and 0 for others).
Here's a summary of the numeric notation for different combinations of permissions:
0: No permission
1: Execute permission only
2: Write permission only
3: Write and execute permissions
4: Read permission only
5: Read and execute permissions
6: Read and write permissions
7: Read, write, and execute permissions
Changing File Permission:
In Linux, you can use the chmod command to change the file permissions of a file or directory. The chmod command modifies the read, write, and execute permissions for the owner, group, and others.
METHOD-1:
Symbolic Mode:
In symbolic mode, you specify the permissions using a combination of letters and operators. The letters represent the users whose permissions you want to modify, where "u" stands for the owner, "g" stands for the group, and "o" stands for others. You can also use "a" to represent all users.
The operators are used to modify the permissions. The plus sign (+) adds the specified permissions, the minus sign (-) removes the specified permissions, and the equal sign (=) sets the specified permissions.
For example,

Here You can see I have a file name "abhi" having the permission of r & w for the user, r & w for the group, and only r for others:
What If I want to change my user permission to rwx which means all Read, Write & Executable?
I will use chmod u+x compare.sh, where abhi is file name :
COPY
chmod u+x compare.sh

here you can see, now the compare.sh file have all r,w, and x permission for the user:
What if I want to remove read and executable permission from the file compare.sh
we use chmod u-rx compare.sh, it will remove that permission:
COPY
chmod u-rx compare.sh

what if I want to give Read permission for both User/owner and group for file compare.sh

METHOD-2:
Numeric Mode:

here, you can see I have a directory name directory1 having the permission of r,w,x for all owners, groups and others.
What if I want to give only read permission to the owner, read and write to the group and no permission for others?
As we know Read denotes 4, write with 2 and execute with 1, so If I want to give read permission for the owner we use 4, for read and write for group 4+2, and 0 for other.
COPY
chmod 460 Sec

What if I want to give read permission for the group and no permission for both owner and other?
we use chmod 040 directory1
COPY
chmod 040 Sec

Changing Ownership of File :
hanging the ownership of a file in Unix-like operating systems can be a crucial task, especially when there is a need to transfer the ownership of a file to another user or group. Changing the ownership of a file can be done through the command line using the chown command. In this blog, we will discuss how to change the ownership of a file in Unix-like systems.
Before we begin, it's essential to understand what file ownership is and why it matters. In Unix-like systems, every file has an owner and a group owner associated with it. The owner is the user who created the file, and the group owner is the group to which the owner belongs. These permissions are important because they determine who can access the file and what actions they can perform on it.

Usage of "CHOWN " Command:
here, we can see, the owner of file name filex is the root, what if I want to change it to other users like ubuntu:
COPY
chown ubuntu:root file1.sh

here, I have to change the ownership to my other user like ubuntu, but what If I want to change for both owner and group:
COPY
chown ubuntu:ubuntu file1.sh

Usage of "CHGRP" Command:
The chgrp command is used to change the group ownership of a file or directory in Unix-like operating systems. It is useful when you want to change the group that can access a particular file or directory.
In Unix-like systems, every file and directory has an owner and a group owner. The owner is the user who created the file or directory, and the group owner is the group to which the owner belongs. The group owner of a file or directory can control the group's access to the file or directory.
The chgrp command can be used to change the group ownership of a file or directory to a specific group. This can be useful in a variety of scenarios, such as:
Managing file access: You can change the group ownership of a file to a specific group, allowing only the members of that group to access the file. This can be useful when you want to limit access to specific files.
Collaboration: When working on a project with a group of people, you may want to share files among the group. By changing the group ownership of the files to the group, all members of the group can access the files without any permission issues.

COPY
chgrp root file1.sh
Here, I change the group ownership from ubuntu to root again using chgrp command.
Access Control List:

Access Control List (ACL) is a security feature in Unix-like operating systems that provides a finer level of access control to files and directories. ACLs extend the traditional Unix file permissions by allowing additional users and groups to be granted access to files and directories. ACLs are used to give more specific permissions to users and groups for accessing files and directories.
The getfacl command is used to view the ACLs of a file or directory.
COPY
getfacl <filename>

Note: You may need to install ACL first to execute this command:
COPY

The setfacl command is used to modify the ACLs of a file or directory.
COPY
setfacl [options] [acl_entries] filename
Access Control List (ACL) is a security feature in Unix-like operating systems that provides a finer level of access control to files and directories. ACLs extend the traditional Unix file permissions by allowing additional users and groups to be granted access to files and directories. ACLs are used to give more specific permissions to users and groups for accessing files and directories.
The getfacl and setfacl commands are used to view and modify ACLs in Unix-like operating systems.
The getfacl command is used to view the ACLs of a file or directory. The basic syntax of the command is:
COPY
cssCopy codegetfacl [filename]


In the above command, replace the filename with the name of the file or directory you wish to view the ACLs of. For example, to view the ACLs of a file named example.txt, you would use the following command:
COPY
Copy codegetfacl example.txt
The output of the getfacl command displays the ACL entries for the file or directory in a user-friendly format.
The setfacl command is used to modify the ACLs of a file or directory. The basic syntax of the command is:
COPY
setfacl [options] [acl_entries] filename
In the above command, options are used to specify any additional options for the setfacl command, such as -m to modify existing ACL entries or -x to remove existing ACL entries. acl_entries specify the new ACL entries to be added to the file or directory. Finally, the filename is the name of the file or directory whose ACLs are to be modified.

here, you can see initially ubuntu users have all read, write and execute permission and I change owner permission to read-only using the following command:
COPY
setfacl -m u: :r file.sh
what if I change the group permission to read only too, for this use the following command:
COPY
setfacl -m g: :w file.sh

here, Initially, it has rwx permission for the group and then changes it to read-only.
ACL (Access Control List) is considered a best practice for several reasons:
Fine-grained control: ACL allows you to define permissions on a per-user or per-group basis. This means you can provide more granular access control to resources than traditional UNIX file permissions that only support three levels of permissions (owner, group, and others).
Flexibility: ACLs allow you to modify permissions on a per-file basis, which is not possible with traditional UNIX file permissions. This means you can give a user or group access to a specific file without having to change permissions for the entire directory.
Improved security: ACLs allow you to control access to files and directories at a much more granular level, which can help prevent unauthorized access and data breaches. Additionally, ACLs provide an additional layer of security, allowing you to set permissions beyond what traditional UNIX file permissions offer.
Audit trail: ACLs provide an audit trail of who has accessed a particular file or directory and what actions were performed. This can be very useful for tracking down the source of security breaches or unauthorized access attempts.
Compliance: Many regulatory compliance frameworks (e.g., HIPAA, PCI DSS) require more granular access control than traditional UNIX file permissions provide. ACLs can help organizations meet these compliance requirements.
2